Mind the Gap between the Code and the Platform with DRIFTCTL
Scroll DownOne of the biggest challenges in an IaC managed infrastructure is to spot drift. Drift is the term that real-world state of your infrastructure differs from the state defined in your configuration. It is a blind spot and a source of potential security issues. Drift can have multiple causes: from team members creating or updating infrastructure through the web console without backporting changes to Terraform, to uncontrolled updates on the cloud provider side. Terraform cannot detect drift of resources and their associated attributes that are not managed using Terraform.
Driftctl is a free and open-source CLI that warns of infrastructure drift and measures infrastructure as code coverage.
Features
- Scan cloud provider and map resources with IaC code
- Analyze diff, and warn about drift and unwanted unmanaged resources
- Allow users to ignore resources
- Multiple output formats
Installation
Driftctl is available on Linux, macOS and Windows. https://docs.driftctl.com/0.38.0/installation (for more details click the link)
Authentication
To use driftctl, we need credentials to make authenticated requests to AWS. Driftctl supports IAM role as an authorization tool, which is considered a good practice and then defining a profile for the role in your ~/.aws/config file. https://docs.driftctl.com/0.38.0/providers/aws/authentication (for more details click the link)
Usage
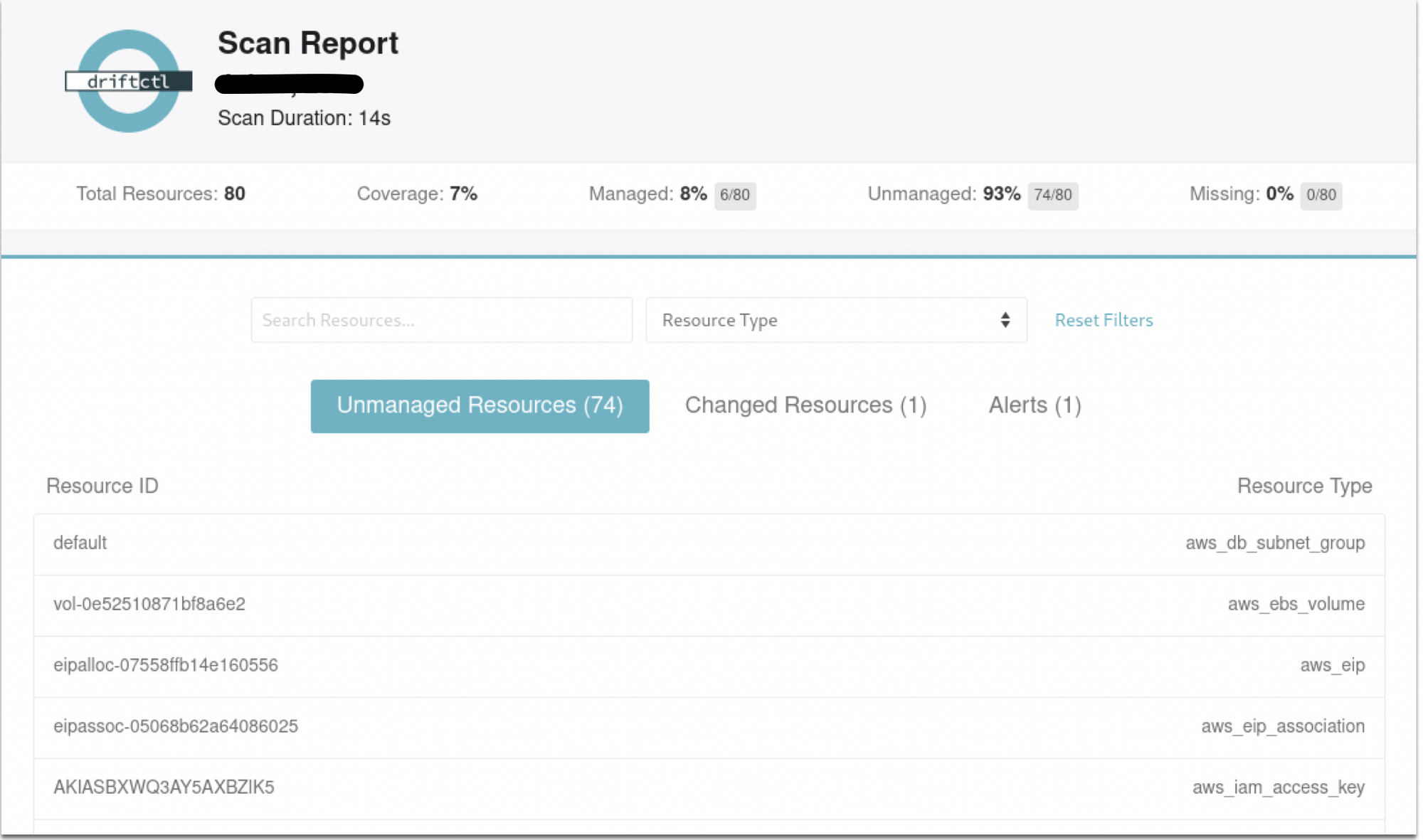
Once you configured your AWS credentials and assign proper permissions , run driftctl scan command to scan resources from the input Terraform statefile and compare it to your current profile infrastructure.
for generating driftcl report locally, use below command and it will generate report.html file and open it with your favorite browser.
AWS_PROFILE=profile_name driftctl scan --from "tfstate+s3://path/to/**/*.tfstate” --output html://report.html
You can integrate driftctl in Jenkins and setup a scheduled job to detect drifts as they happen. To quickly share & easily access reports across the team, we can store daily HTML reports on an S3 bucket and generate pre-sign url out of it.
pipeline {
agent any
options {
skipDefaultCheckout()
timestamps()
ansiColor('xterm')
}
environment {
WORKSPACE = pwd()
AWS_PROFILE = "${PROFILE}"
}
stages {
stage('Driftctl scan') {
steps {
script {
sh "mkdir -p /tmp/driftcl/reports/"
dir("tmp/driftcl/reports/") {
sh "driftctl scan --from 'tfstate+s3://bucketname1/**' -o html://driftctl-report.html || true"
sh "aws s3 cp driftctl-report.html s3://bucketname/"
sh "rm -rf driftctl-report.html"
}
}
}
}
}
***note
Quotes are required for glob patterns to match multiple state files at once.
AWS_PROFILE=profile_name driftctl scan --from "tfstate+s3://path/to/**/*.tfstate” --output html://report.html
.driftignore generator
driftctl provides a command to automatically generate a .driftignore file from a previous scan given the type of resources you want to exclude (e.g. unmanaged, missing or changed resources)
driftctl scan --from tfstate://statefile -o json://result.json
driftctl gen-driftignore -i result.json
You can filter which kind of resource you want to ignore using these flags:
--exclude-unmanaged: Exclude resources not managed by IaC--exclude-missing: Exclude resources missing on cloud provider--exclude-changed: Exclude resources that changed from IaC

View Comments