Integrate AWS IAM Identity Center(SSO) SAML with for Amazon OpenSearch Dashboard
Scroll Down
Amazon OpenSearch Service is an AWS-managed service that lets you run and scale OpenSearch clusters without having to worry about managing, monitoring, and maintaining your infrastructure, or having to build in-depth expertise in operating OpenSearch clusters.
SAML based federation for OpenSearch & Dashboards will make use of any existing identity provider (IdP) to enable Single Sign On. It also gives you fine-grained access control, and the ability to search data and build visualisations.
Amazon OpenSearch supports provider that uses the SAML 2.0 standard, such as AWS IAM Identity Center(AWS SSO), Auth0, Okta, Keycloak, Active Directory Federation Services (AD FS), and Ping Identity (PingID).
In this post I will go through how to Integrate AWS IAM Identity Center with Opensearch.
Authentication Flow:

- User opens browser window and navigates to OpenSearch Dashboards
- OpenSearch Service generates SAML authentication request
- OpenSearch Service redirects request back to browser
- Browser redirects to IAM Identity center URL
- AWS IAM Identity center parses SAML request, authenticates user, and generates SAML response
- AWS IAM Identity center returns encoded SAML response to browser
- Browser sends SAML response back to OpenSearch Service Assertion Consumer Service (ACS) URL
- ACS verifies SAML response
- User logs into OpenSearch Service domain
Lets get Started
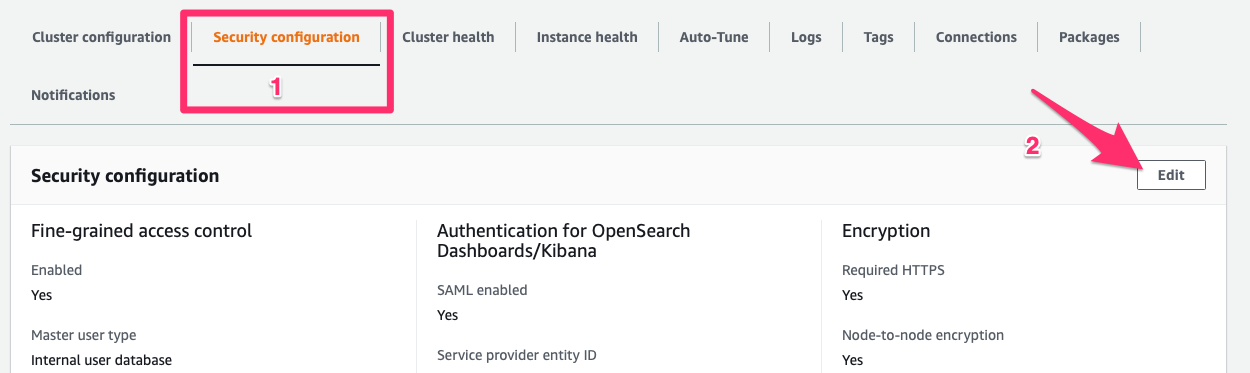
Create a AWS OpenSearch Domain and make sure you enable fine-grained access control, this will allow us to use SAML Configuration.
To configure SAML Authentication Domain need to created & it should be running.
we can the SAML Authentication by editing the Cluster Security.
Copy below two properties after enabling the SAML, which we will use in AWS IAM Identity Center
- Service provider entity ID
- IdP-initiated SSO URL
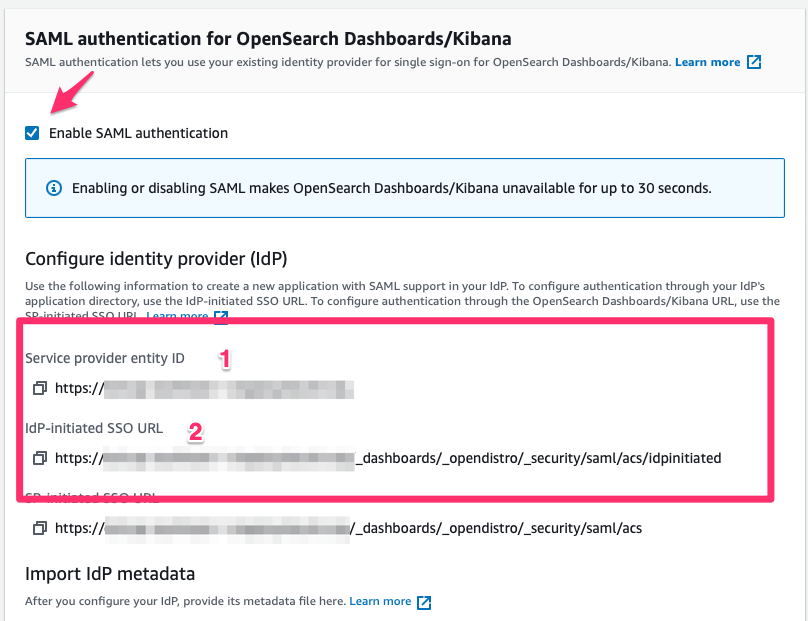
Leave this page open, we will come back to this later.
Configuration Of IAM Identity Center to setup SAML 2.0
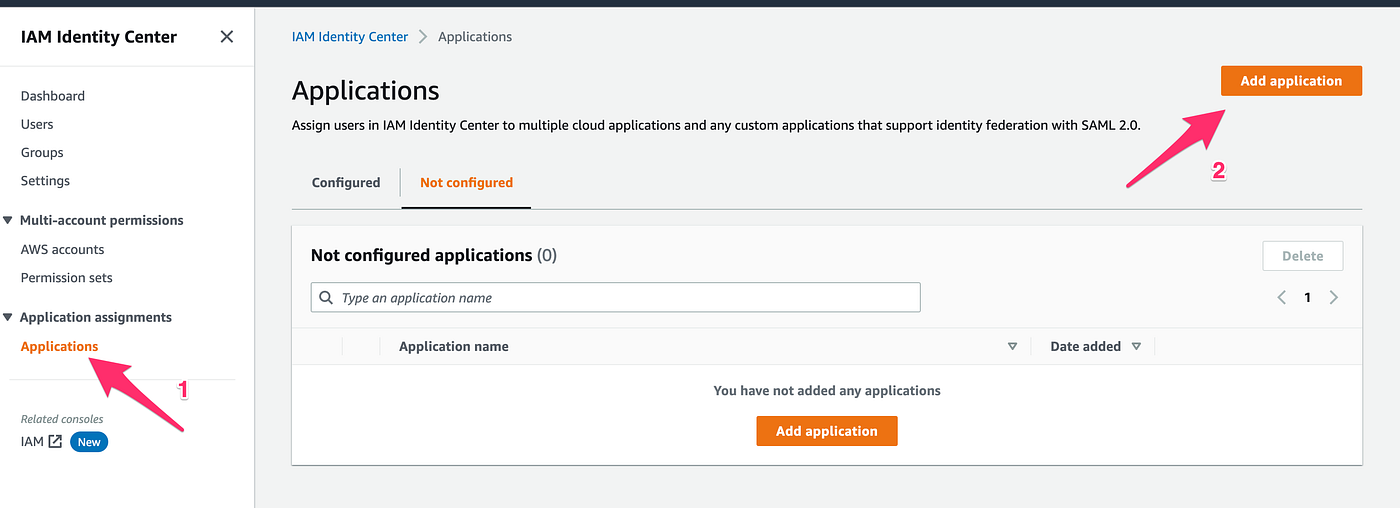
- Open the IAM Identity Center console.
- Choose Applications.
- Choose Add application.
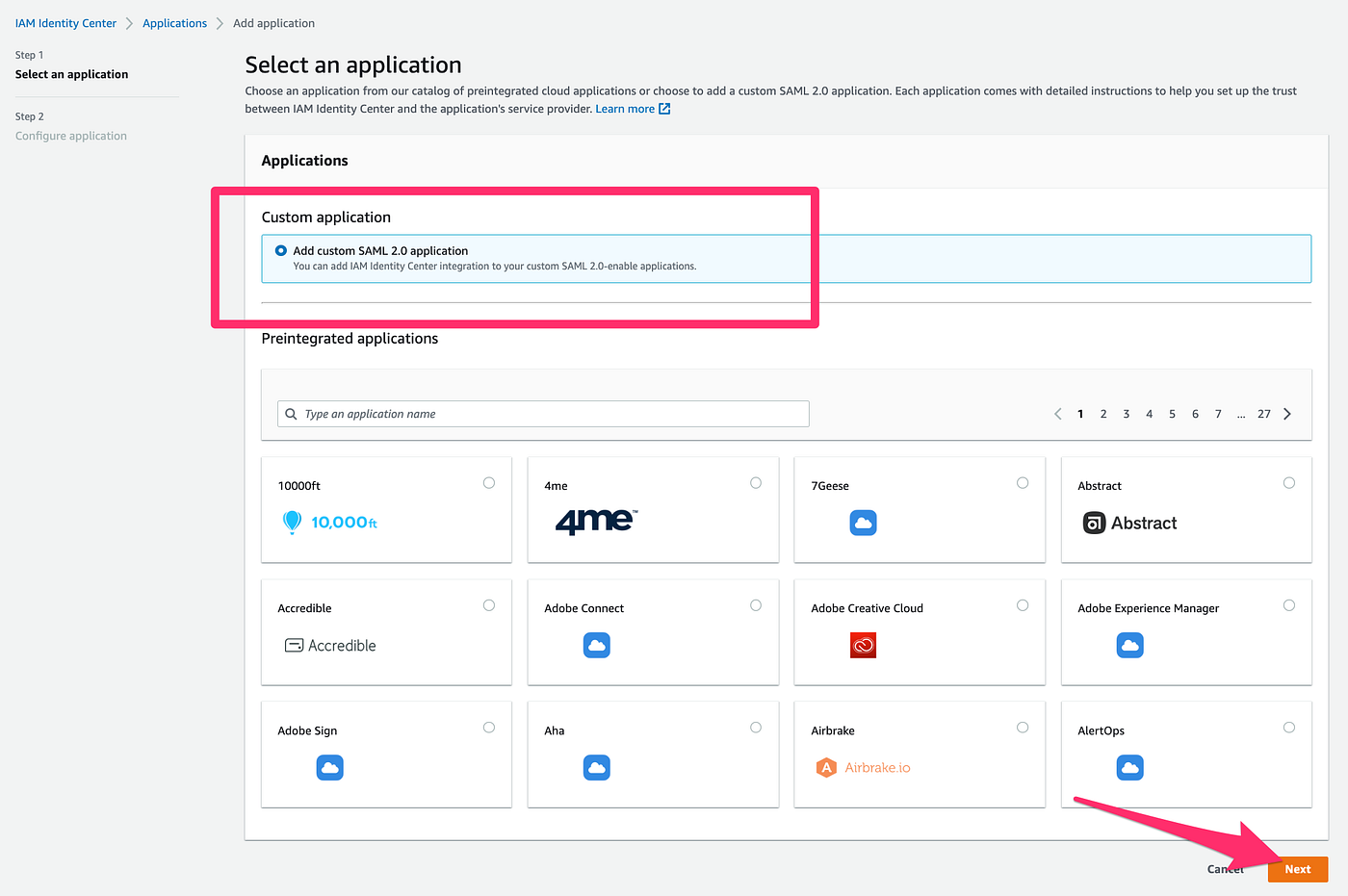
4. On the Select an application page, choose Add custom SAML 2.0 application. Then, choose Next.
5. On the Configure application page, under Configure application, enter a Display name for the application as OpenSearch.
6. Under IAM Identity Center metadata, Click Download to get the SAML Metadata file.

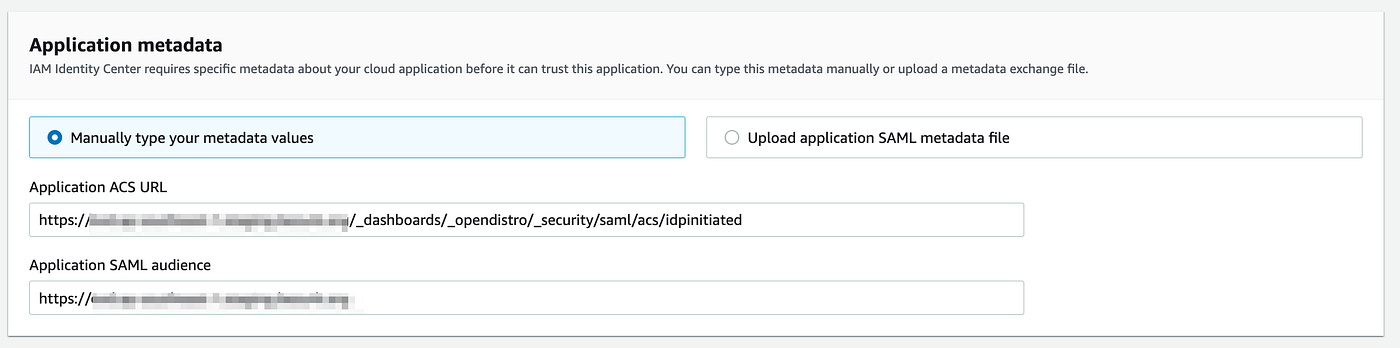
7. Under Application metadata, choose Manually type your metadata values. Then, provide the Application ACS URL and Application SAML audience values which we copied from the opensearch and click submit
Application ACS URL → IdP-initiated SSO URL
Application SAML audience → Service provider entity ID
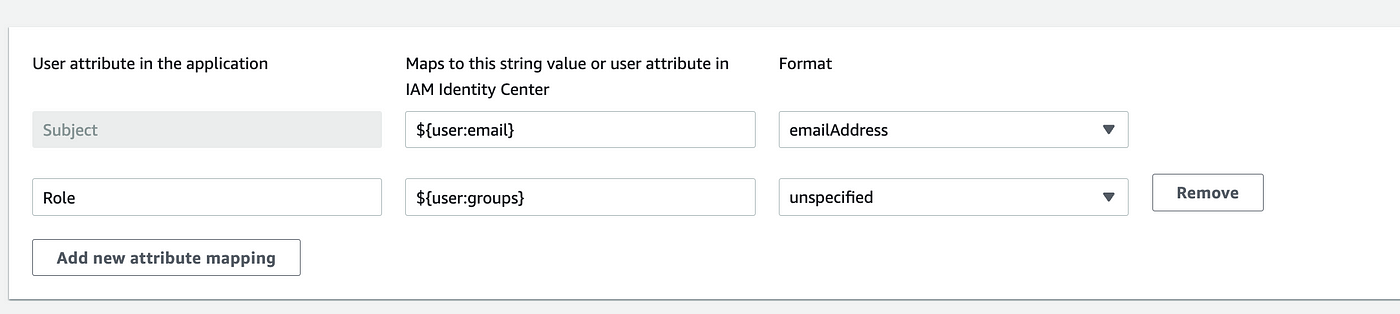
8. Click Edit attribute mappings, and map values as below and save changes
Subject -> ${user:email} -> emailAddress
Role -> ${user:groups} -> unspecified

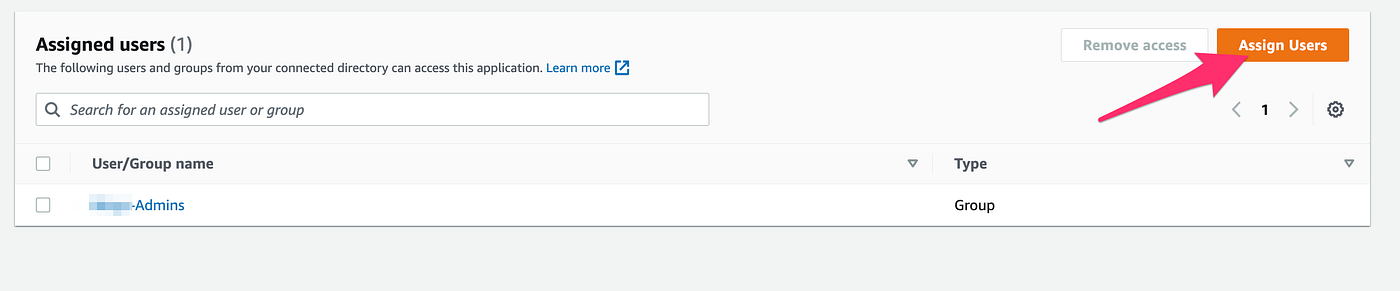
9. Click Assign Users & Click select any group which you would like to give access for Dashboard. If you don’t have any group, Create a new one.
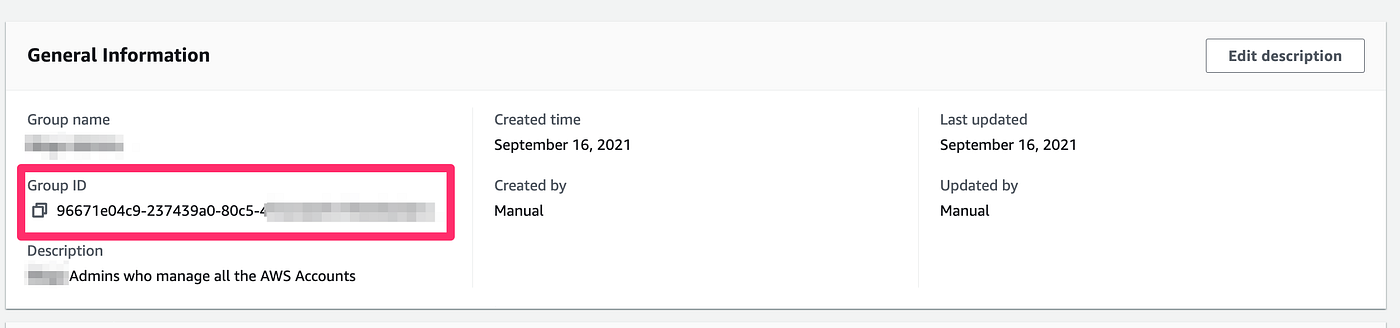
10. Copy the Group ID of the SSO Group which was added.
We have completed the AWS IAM Identity Center configuration. Let’s go back to the Opensearch Page.
- Upload/ Paste the IDP metadata which we download from the AWS IAM. It will auto populate the IdP entity ID (don’t change anything).
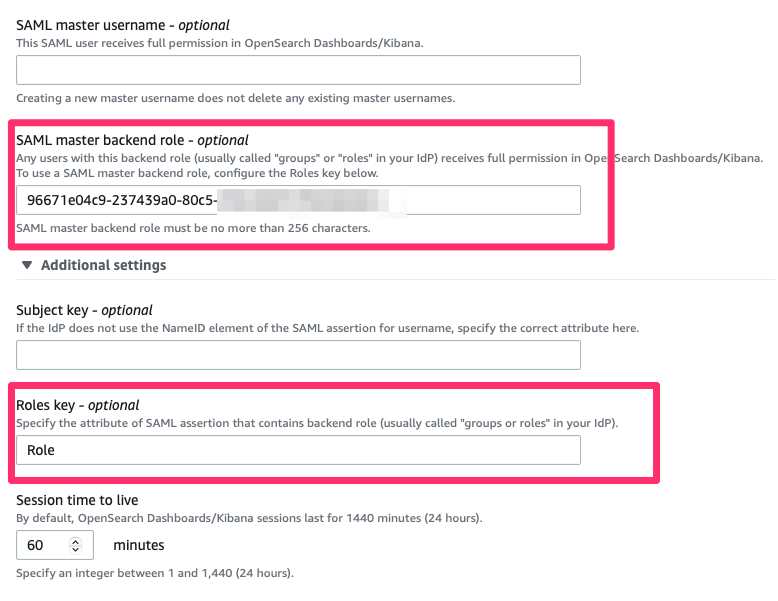
- Copy the group ID into SAML master backend role, This will make sure all the member of this group assigned a Admin to Openseach/Dashboard.
- Mention Role under Roles Keys to extract the the groups from AWS SSO and click save changes.
Note: We have mapped this Role in AWS SSO under Edit Attribute Mapping.
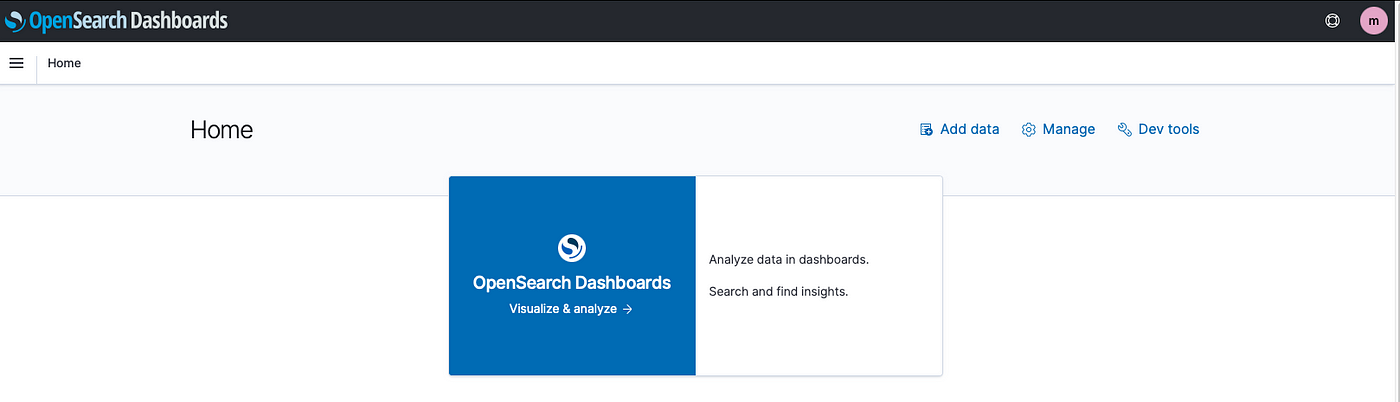
All the configuration is done, let’s test the configuration.
Open AWS SSO Landing page, Now you should be able to see the Application which we added, Click on that, it will authenticate and open the Dashboard.
In dashboard navigate to security -> role and search for all_access & security_manager, you can notice the group id was added by opensearch configuration.
Conclusion
In this blog post, we have demonstrated how to set up AWS IAM Identity Center as an identity provider over SAML authentication for OpenSearch Dashboards access. This will streamline single login process and improves productivity.

View Comments