IAM access gets more complicated when we want to allow access to a client/application which needs access outside of the AWS cloud.
Disadvantage in using IAM Keys
- AWS keys will be a long lived credentials
- Frequent rotation of IAM keys
AWS IAM Roles Any where is a newly released AWS service that allows us to use private key infrastructure (PKI) to generate temporary credentials for accessing IAM roles from outside of AWS world.
What is AWS IAM Roles Anywhere ?
- It used to get temporary AWS credentials that allow access to your AWS resources in shot lived period.
- It gives access based on x.509 certificates and the PKI, where on-premises servers use client certificates, signed by a certificate authority (CA) that can control and registered in “AWS IAM Role Anywhere”.
Pre-requisite:
- Private Certificate Authority
- AWS signing helper
How to Create Private Certificate Authority/Private Key Infrastructure
There is two option to create PCA/PKI:
- AWS Certificate manager to create Private Certificate Authority (ACM PCA) which is simple way to create, but it comes with its own pricing. Each PCA costs $400.
- Create own certificate authority using openssl, cfssl, vault PKI.
I have chosen CFSSL, this was created by CloudFlare to manage my private CA.
cfssl can be installed based on the operating system
#Mac
brew install cfssl
#Ubuntu
sudo apt-get -y install golang-cfsslCreate ca.json file to generate the certificate signing request. This is the example I am using for my certificate authority.
{
"hosts":[
"iamadan.com"
],
"key":{
"algo":"rsa",
"size":2048
},
"names":[
{
"C":"India",
"ST":"Tamilnadu",
"L":"Chennai",
"O":"Custom CA",
"OU":"Duolc"
}
]
}Run the following command to generate CA.
cfssl gencert -initca ca.json | cfssljson -bare ca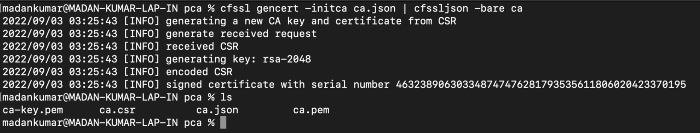
Configure IAM Roles Anywhere
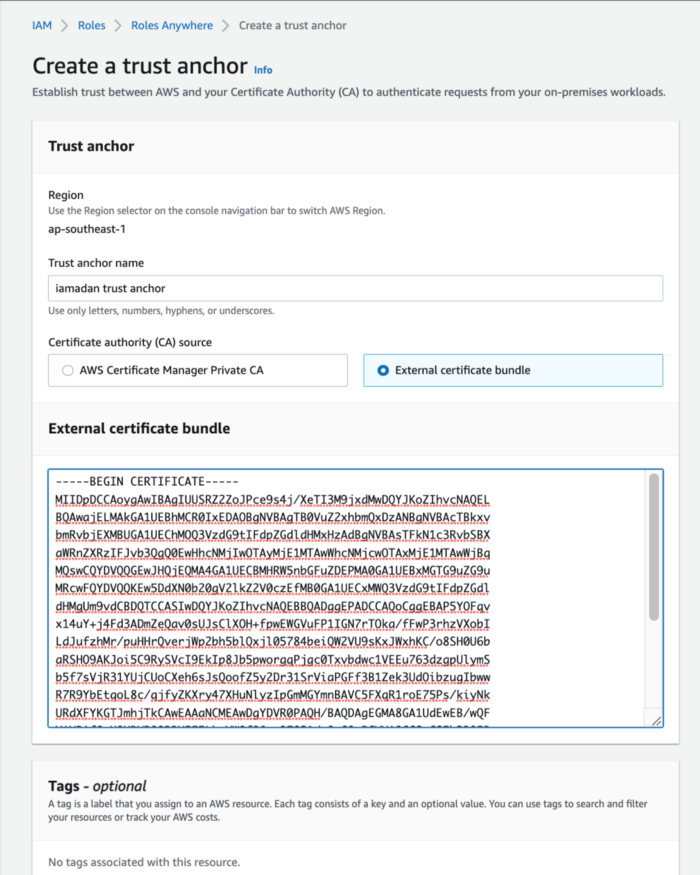
- Create Trust Anchor
- Open the AWS IAM console, go to Roles and at the bottom, under the Roles Anywhere section, click Manage.
- Click Create a trust anchor and fill in the anchor name.
- Select External certificate bundle.
- Under External certificate bundle, paste CA certificate which created in our previous step. Get the content of ca.pem
- Click Create trust anchor.
Configure IAM Roles Anywhere
- Create Trust Anchor
- Open the AWS IAM console, go to Roles and at the bottom, under the Roles Anywhere section, click Manage.
- Click Create a trust anchor and fill in the anchor name.
- Select External certificate bundle.
- Under External certificate bundle, paste CA certificate which created in our previous step. Get the content of ca.pem
- Click Create trust anchor.
2. Create a Role That Trusts the IAM Roles Anywhere Service Principal
Need to create an IAM role that trust the IAM Roles Anywhere service and provide clients with permissions. We can narrow down permissions by allowing only client certificates with “OU=Duolc” in their subject
Note: Change the OU based on your configuration.
- Go to IAM -> Roles -> Create Role.
- Select Custom Trust Policy and paste the following policy as the Custom trust policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "rolesanywhere.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:TagSession",
"sts:SetSourceIdentity"
],
"Condition": {
"StringEquals": {
"aws:PrincipalTag/x509Subject/OU": "Duolc"
}
}
}
]
}- Select managed policy “AmazonS3FullAccess” and select it.
- Give name for the role and click Create Role
3. Create Profile under IAM Roles Anywhere
Create a profile in which we specify which IAM roles in our account we want to allow clients to assume via temporary credentials.
- Roles Anywhere -> Create a profile and provide a name for the profile.
- Under Roles -> select perviously created role.
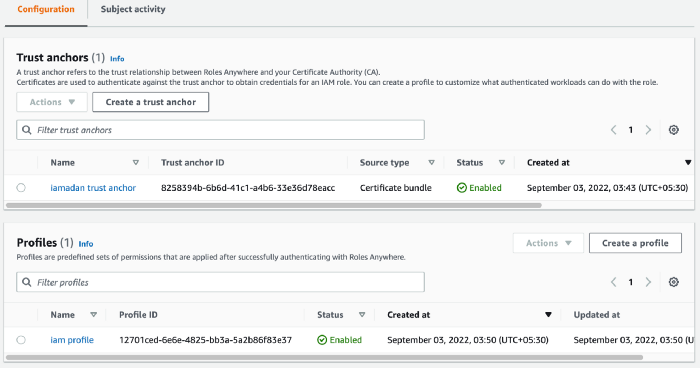
Once the IAM Roles Anywhere has been configured, lets generate certificates for authentication.
Let’s use the cfssl tool to sign a certificate for my role. create another file csr.json
{
"CN": "iamaw.iamadan.com",
"names":[
{
"C":"India",
"ST":"Tamilnadu",
"L":"Chennai",
"O":"Custom CA",
"OU":"Duolc"
}
]
}Run the following command to generate Certificates for authentication.
cfssl gencert -ca ca.pem -ca-key ca-key.pem csr.json| cfssljson -bare iamaw.iamadan.com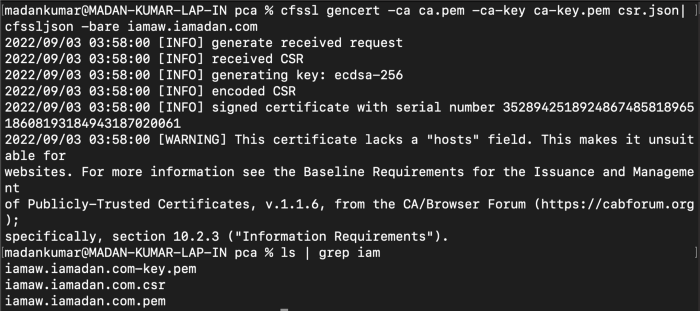
Time to put altogether and test it
To use our client certificate to obtain temporary credentials, we have to use the “AWS Signing Helper utility”, which you can download here.
Move the aws_signing_helper binary to one of the listed locations. This command assumes that the binary is currently in your downloads folder and that your PATH includes /usr/local/bin, but can customize it if your locations are different.
echo $PATH
mv ~/Downloads/aws_signing_helper /usr/local/bin/- Trust Anchor ARN
- Roles Anywhere Profile ARN
- Role ARN
aws_signing_helper credential-process --trust-anchor-arn arn:aws:rolesanywhere:ap-southeast-1:12345689767:trust-anchor/8258394b-6b6d-41c1-a4b6-33e36d78eacc --profile-arn arn:aws:rolesanywhere:ap-southeast-1:12345689767:profile/12701ced-6e6e-4825-bb3a-5a2b86f83e37 --role-arn arn:aws:iam::12345689767:role/IAMAnywhere --certificate /Users/madankumar/private-ca/pca/iamaw.iamadan.com.pem --private-key /Users/madankumar/private-ca/pca/iamaw.iamadan.com-key.pemIf you successfully receive a response with the credentials, you can configure an AWS profile on the machine and run awscli commands to test the solution.
cat ~/.aws/config 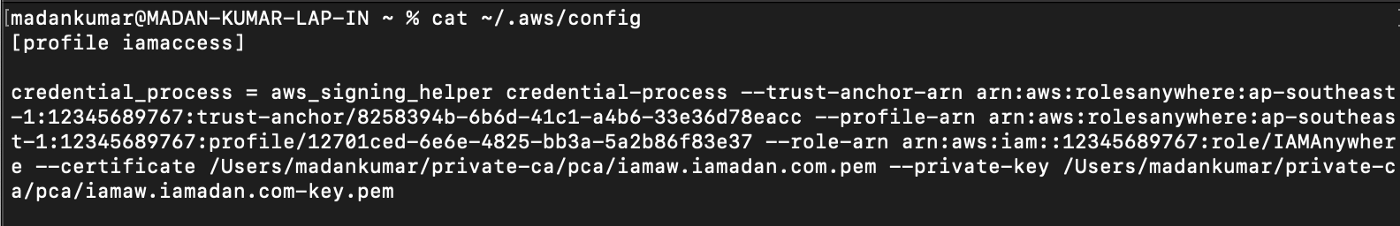
aws s3 ls --profile iamaccessCRL Support for Lost or Compromised Certificates
IAM Roles Anywhere also supports certificate revocation lists (or CRLs), allowing you to revoke lost or compromised certificates.
Happy Securing !!!!

View Comments