Simplifying tunnel to private network
Scroll DownHow our current ssh config looks like below and it will have multiple line of local forward to tunnel the traffic.
Host pg
User admin
HostName 18.139.62.211
Port 22
ForwardAgent yes
LocalForward localhost:6767 xxx-db.ap-southeast-1.production.org:5432
LocalForward localhost:9898 yyyy-db.ap-southeast-1.production.org:443
LocalForward localhost:9999 zzzz-db.ap-southeast-1.production.org:80
LocalForward localhost:3308 ppp-db.ap-southeast-1.production.org:3306What's the problem with above configuration? everything works good !
The above configuration will work awesome and there is no issue with it when we have few LocalForwards. Problem arise when have more number of LocalForwards, in our case we will have staging LocalForwards and production LocalForwards.
Disadvantage of having more LocalForward
- Every new service in private network need to be added in ssh config
- Need to remember the forward port
- Need to check available local forward port to avoid collision
SSHUTTLE ( VPN Over SSH )
sshuttle is a transparent proxy server that works as a VPN over ssh. The only requirement on the client side is that the host must have Python available. This is because sshuttle constructs and runs some Python source code to help transmit data.
Install sshuttle using brew in mac
brew install sshuttleInstall sshuttle in linux
apt-get install sshuttlefor more installation checkout github https://github.com/sshuttle/sshuttle
Make a copy of current ssh config
mv ~/.ssh/config ~/.ssh/config-bakupCreate a new SSH config with the config below
vi ~/.ssh/confighost i-*.* mi-*.*
ProxyCommand bash -c "aws ssm start-session --target $(echo %h|cut -d'.' -f1) --profile $(echo %h|/usr/bin/cut -d'.' -f2) --document-name AWS-StartSSHSession --parameters 'portNumber=%p'"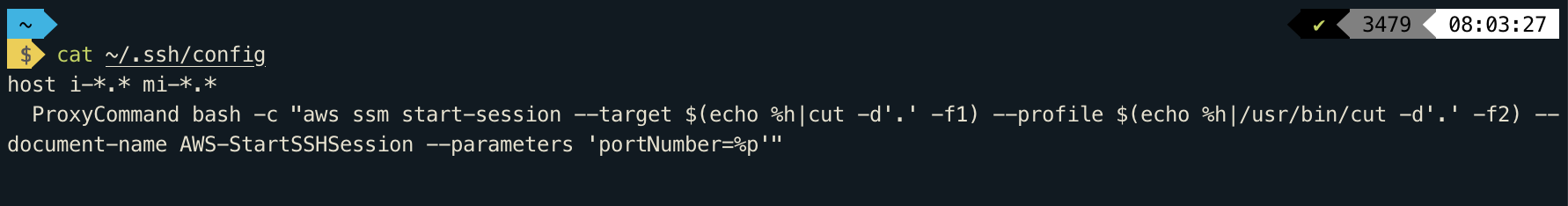
yes that's it, no other config is required in ssh config, it looks clean and simple.
It time to connect our Blackhole Server.
As you all know how to connect blackhole server, I am skipping this section. If you want to know on how to connect/setup blackhole please checkout this
https://geeks.wego.com/wego-blackhole-access-via-aws-session-manager/
Here is the magical command to forward all the private network.
sshuttle -r wegodev@<ssm-instance-id>.<profile_name> 10.0.0.0/8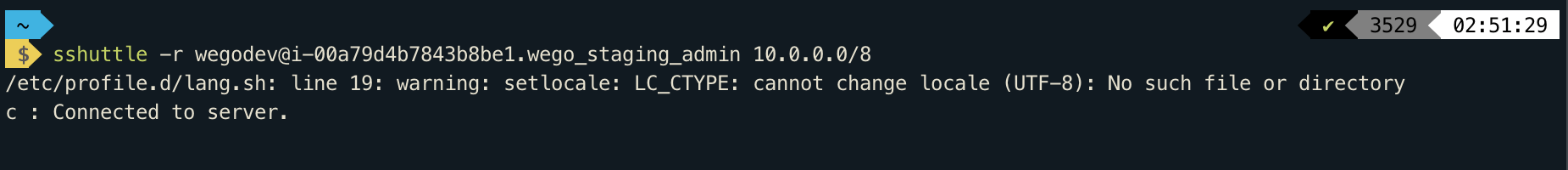
Note: if you want to connect both staging and production simultaneously , open new terminal and run the same command with production instance id and aws profile name.
Yes, now poor man's vpn is up and can connect RDS, Redis, Internal LoadBalance, etc without doing any local forward.
Happy Connecting !!!

View Comments