Wego BlackHole access via AWS Session Manager
Scroll DownBlackhole/Bastion/Jumphost is defined as “a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attack, a bastion host must minimize the chances of penetration.”
AWS Session manager allows one to make an interactive shell connection to an EC2 instance with several key features:
- Instances in private subnets can be connected to even without a NAT gateway being present.
- No inbound security group rules are required for public/private instances, all communication is via the Systems Manager service.
- All user sessions and commands are logged to Cloudwatch logs (or S3) with optional encryption via KMS.
- Access control is via standard IAM policies and can be configured for tag based resource access.
- Deploying and managing ssh-keys for EC2 instances is not necessary.
- SSH can be tunnelled over a session manager session. This can be used to provide access to private RDS, Redis, RabbitMQ, Internal ALB/ELB
Topic
- Client machine Pre-Requisite
- Configure AWS CLI to use Session Manger
Prerequisite in the client machine (MacBook):
- Install/Update AWS CLI version 2
- Install session-manager-plugin
- Install ec2 instance connect cli
Install AWS CLI v2
curl "https://awscli.amazonaws.com/AWSCLIV2.pkg" -o "AWSCLIV2.pkg"
sudo installer -pkg AWSCLIV2.pkg -target /Successful installation should output like below
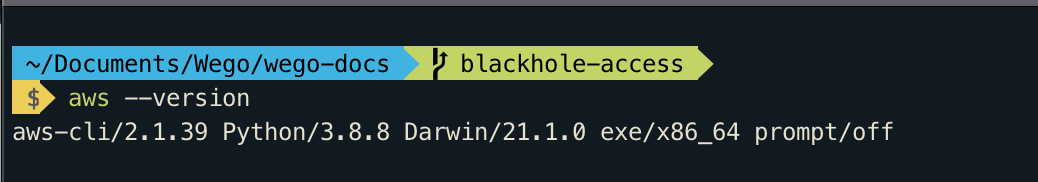
Install session-manager-plugin
curl "https://s3.amazonaws.com/session-manager-downloads/plugin/latest/mac/session-manager-plugin.pkg" -o "session-manager-plugin.pkg"
sudo installer -pkg session-manager-plugin.pkg -target /
sudo ln -s /usr/local/sessionmanagerplugin/bin/session-manager-plugin /usr/local/bin/session-manager-pluginSuccessful installation should output like below
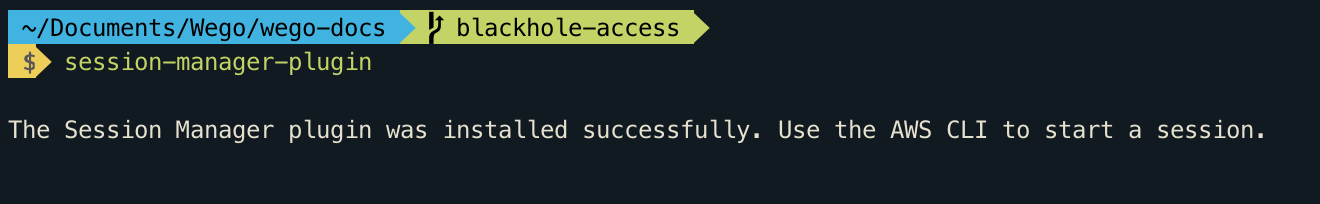
Install ec2 instance connect cli
pip3 install ec2instanceconnectcliConfigure AWS CLI to use Session Manger
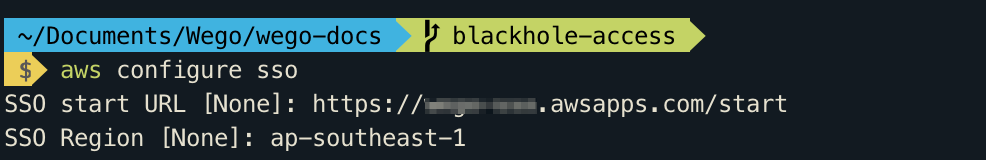
Automatic configuration using the command aws configure sso
You can add an AWS SSO enabled profile to your AWS CLI by running the following command, providing your AWS SSO start URL and the AWS Region that hosts the AWS SSO directory.
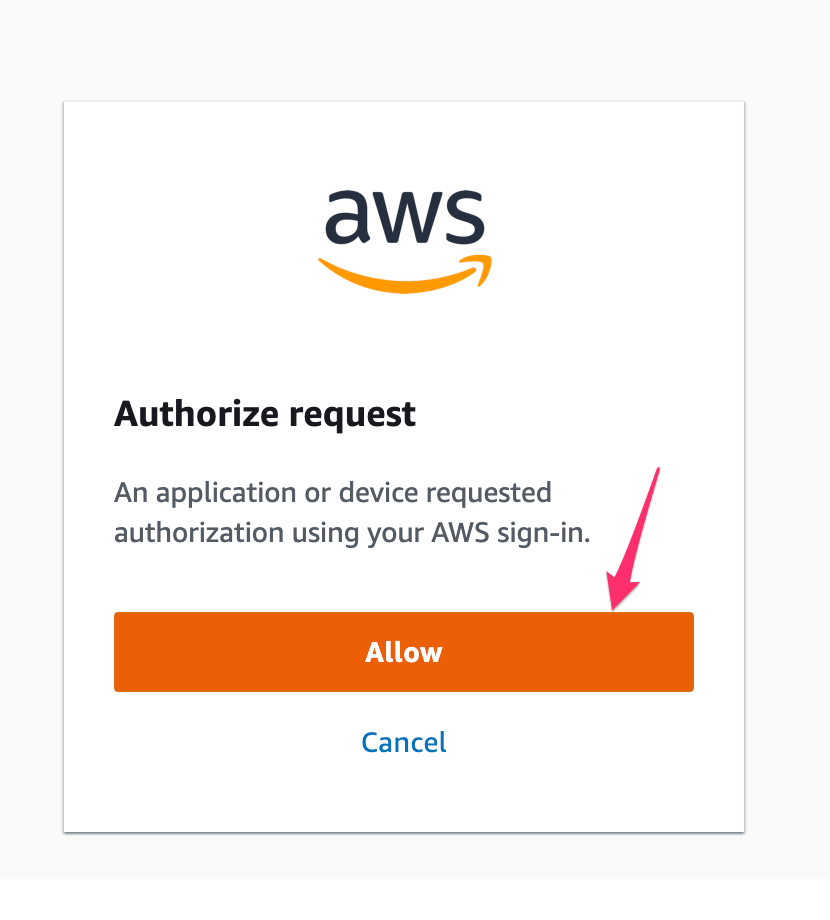
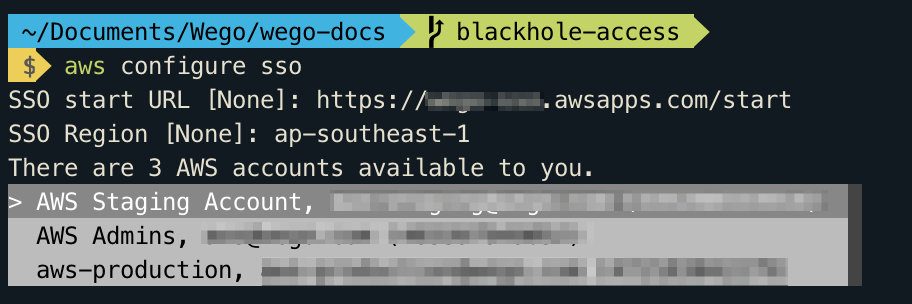
AWS CLI displays the AWS accounts available for you to use. If you are authorised to use only one account, the AWS CLI selects that account for you automatically and skips the prompt. The AWS accounts that are available for you to use are determined by your user configuration in AWS SSO.
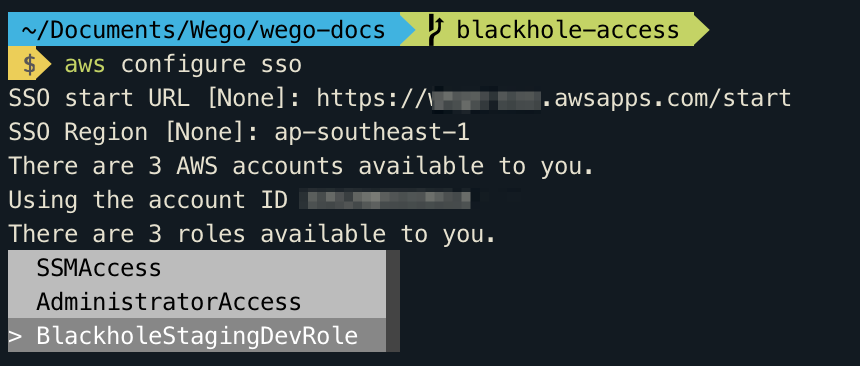
AWS CLI confirms your account choice, and displays the IAM roles that are available to you in the selected account. If the selected account lists only one role, the AWS CLI selects that role for you automatically and skips the prompt. The roles that are available for you to use are determined by your user configuration in AWS SSO.
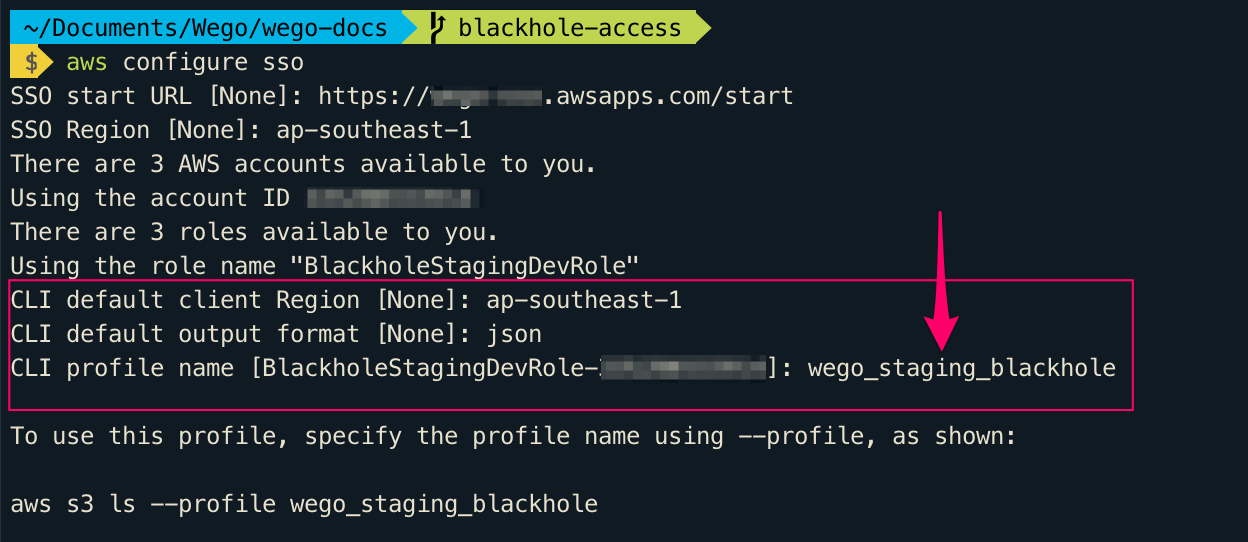
SSH Configuration to use port tunnelling
- Update the SSH configuration file to enable running a proxy command that starts a Session Manager session and transfer all data through the connection.
- The SSH configuration file located at
~/.ssh/config - Add the following to the configuration file on the local machine.
Host stage_tunnel
User wegodev
Hostname i-00a7fdfvb7843b8be1
RequestTTY no
ProxyCommand sh -c "aws ssm start-session --profile wego_staging_blackhole --region ap-southeast-1 --target %h --document-name AWS-StartSSHSession --parameters 'portNumber=%p'"
Localforward 5432 xxxxxx-yyyyy.cf1cz5f00ry8.ap-southeast-1.rds.amazonaws.com:5432- Hostname represents ec2 instance ID here instead of ip or dns
- Please add the
Localforwardparameter as per your need.
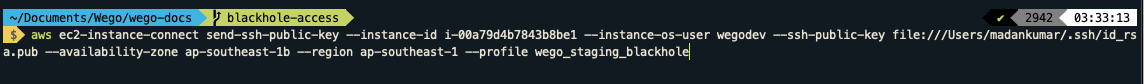
Send the SSH key to the Blackhole Server when you want to do ssh tunnel.
aws ec2-instance-connect send-ssh-public-key --instance-id i-00a7fdfvb7843b8be1 --instance-os-user wegodev --ssh-public-key file:///Users/madankumar/.ssh/id_rsa.pub --availability-zone ap-southeast-1b --region ap-southeast-1 --profile wego_staging_blackholePlease change the file name file:///Users/<username>/.ssh/id_rsa.pub.
This command will copy the key to the server for a short time and it will be deleted automatically when there is no active session.
Once ssh key send to the server, ready to tunnel.
ssh stage_tunnel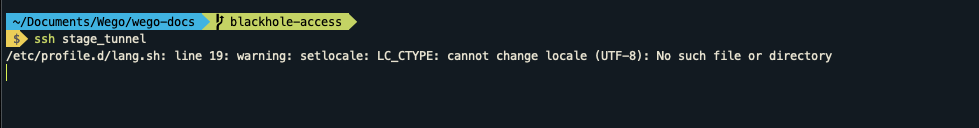
Now we are tunnelled to the private resources using private Instance and without worrying about the SSH key added into machine.
Happy Secure Tunnelling !!!

View Comments